CCNP300-410学习笔记(1-50)
1、Refer to the exhibit. Users in the branch network of 2001:db8:0:4::/64 report that they cannot access the Internet. Which command is issued in IPv6 router EIGRP 100 configuration mode to solve this issue?
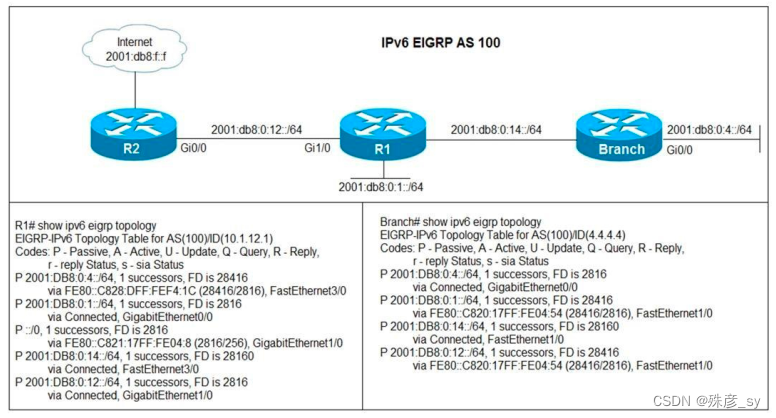
A. Issue the eigrp stub command on R1.
B. Issue the no eigrp stub command on R1.
C. Issue the eigrp stub command on R2.
D. Issue the no eigrp stub command on R2.
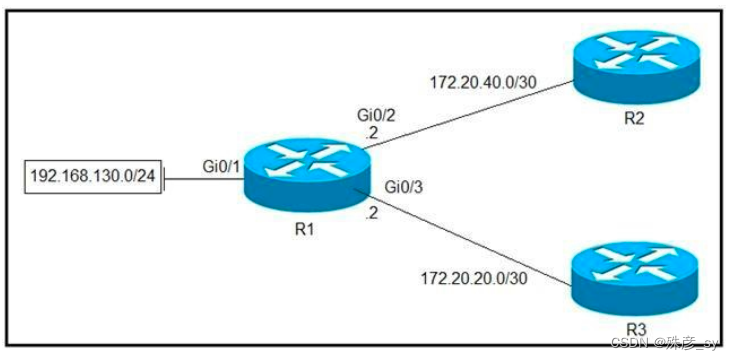
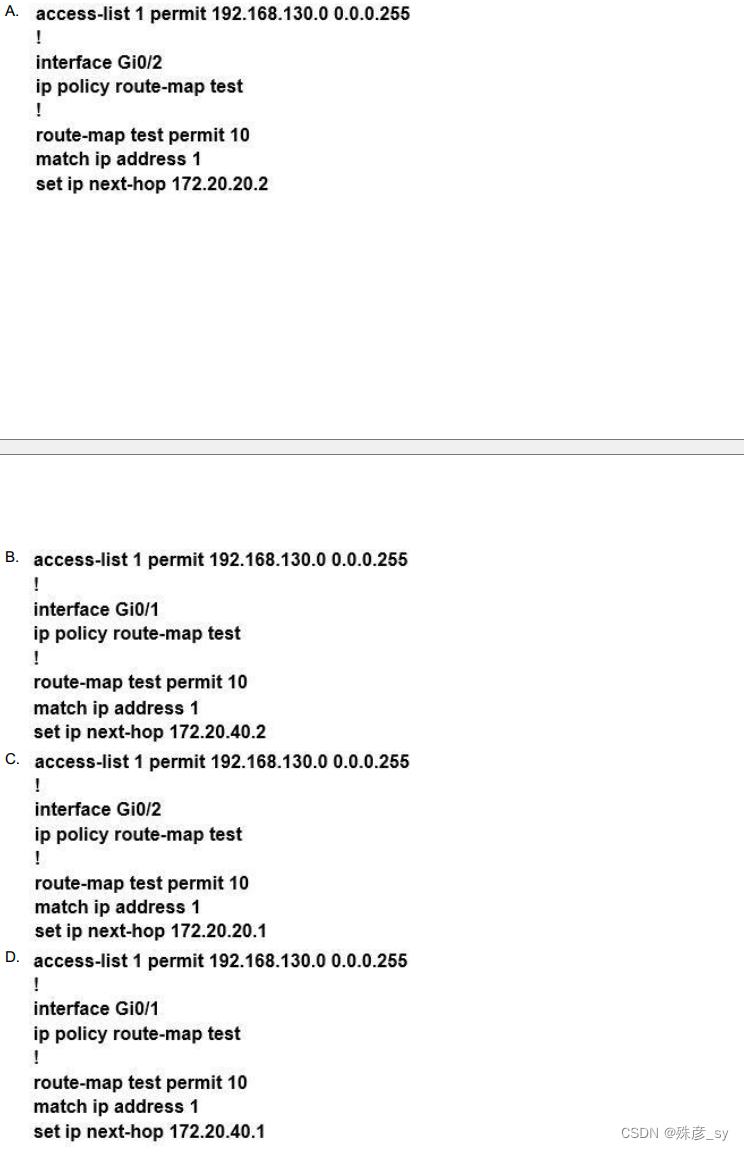
2、 Refer to the exhibit. Which configuration configures a policy on R1 to forward any traffic that is sourced from the 192.168.130.0/24 network to R2? D
3、R2 has a locally originated prefix 192.168.130.0/24 and has these configurations:
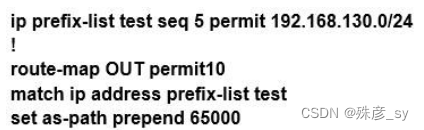
What is the result when the route-map OUT command is applied toward an eBGP neighbor R1 (1.1.1.1) by using the neighbor 1.1.1.1 route-map OUT out command?
A. R1 sees 192.168.130.0/24 as two AS hops away instead of one AS hop away.
B. R1 does not accept any routes other than 192.168.130.0/24
C. R1 does not forward traffic that is destined for 192.168.30.0/24
D. Network 192.168.130.0/24 is not allowed in the R1 table
4、Which method changes the forwarding decision that a router makes without first changing the routing table or influencing the IP data plane?
A. nonbroadcast multiaccess
B. packet switching
C. policy-based routing
D. forwarding information base
5、Refer to the exhibit. The output of the trace route from R5 shows a loop in the network. Which configuration prevents this loop? A
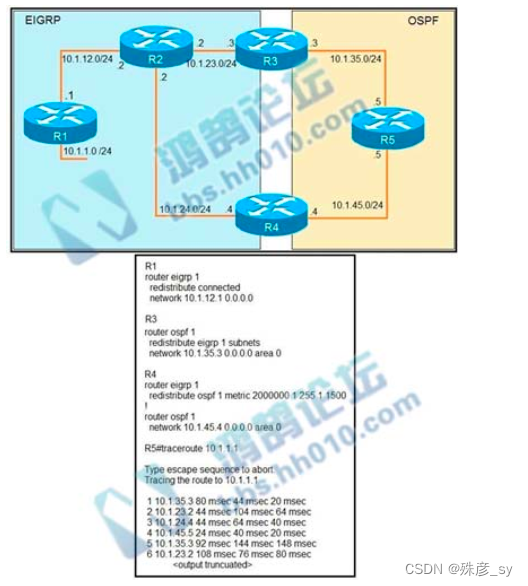
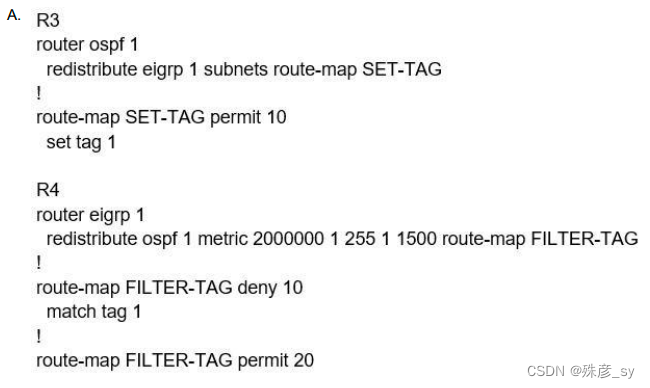
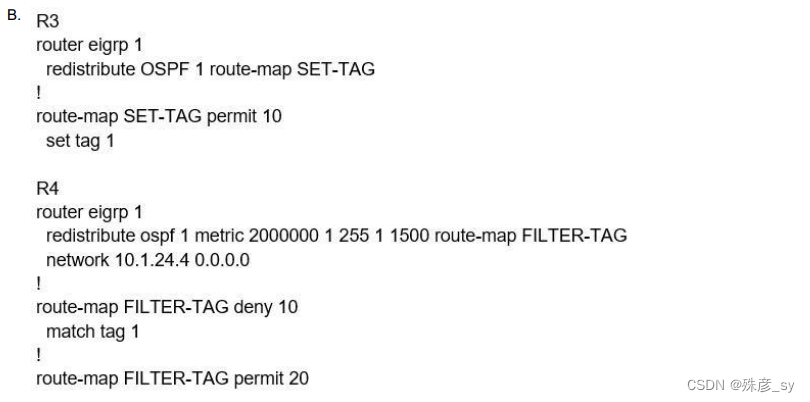
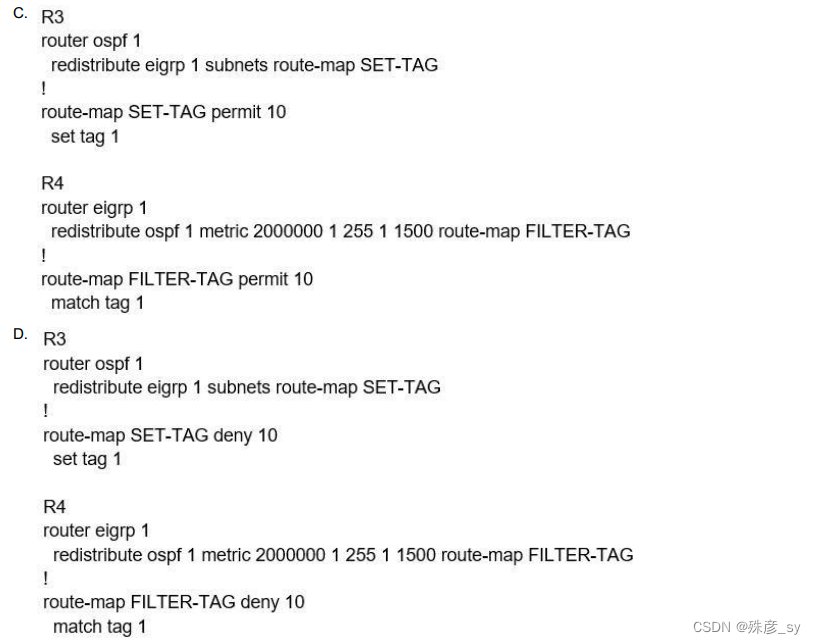
6、Refer to the exhibit. An engineer configures a static route on a router, but when the engineer checks the route to the destination, a different next hop is chosen.
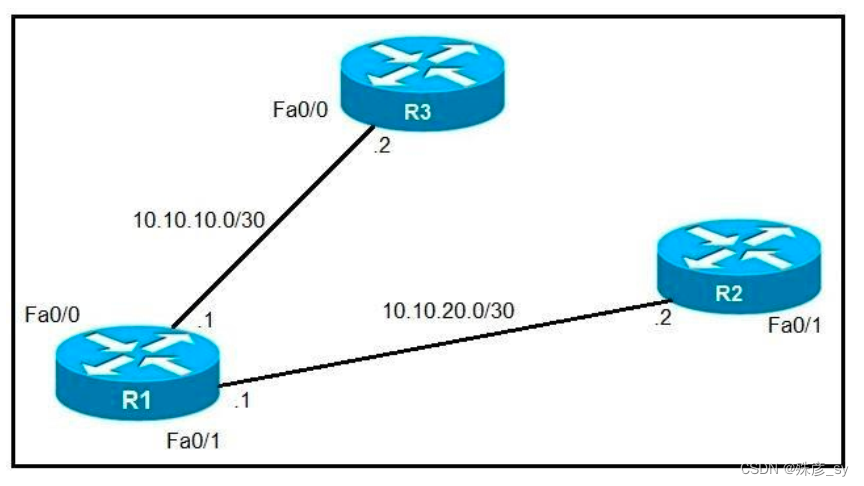
What is the reason for this?
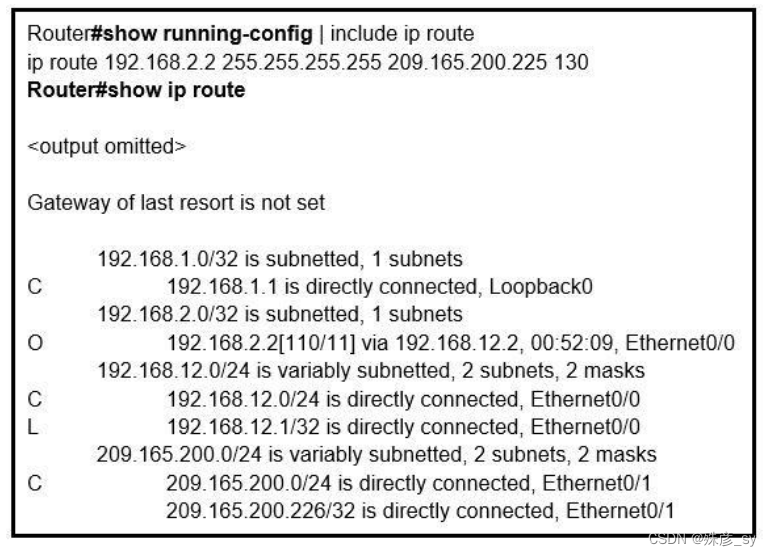
A. Dynamic routing protocols always have priority over static routes.
B. The metric of the OSPF route is lower than the metric of the static route.
C. The configured AD for the static route is higher than the AD of OSPF.
D. The syntax of the static route is not valid, so the route is not considered
7、Refer to the exhibit. An engineer is trying to generate a summary route in OSPF for network 10.0.0.0/8, but the summary route does not show up in the routing table. Why is the summary route missing?
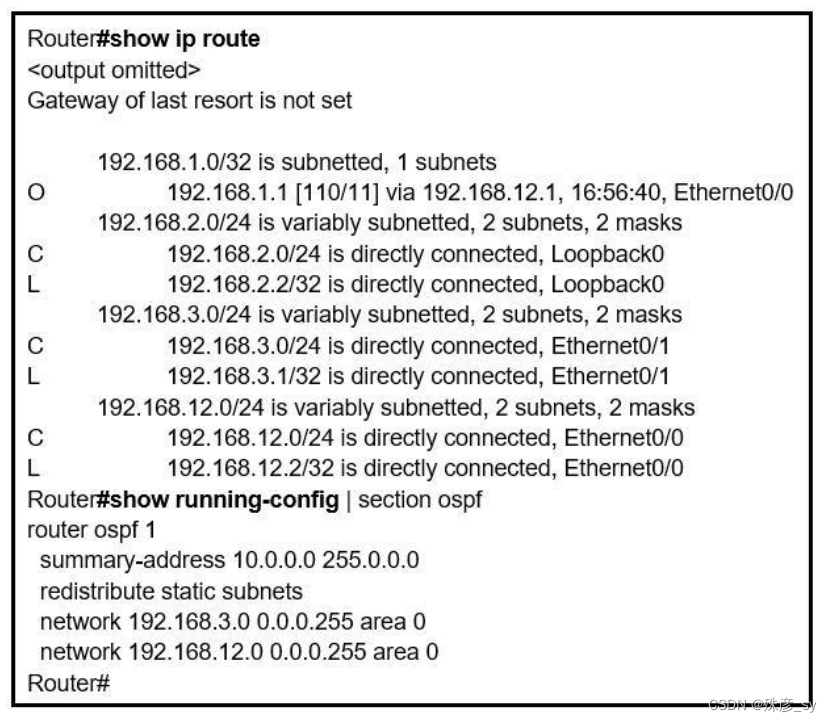 A. The summary-address command is used only for summarizing prefixes between areas.
A. The summary-address command is used only for summarizing prefixes between areas.
B. The summary route is visible only in the OSPF database, not in the routing table.
C. There is no route for a subnet inside 10.0.0.0/8, so the summary route is not generated.
D. The summary route is not visible on this router, but it is visible on other OSPF routers in the same area.
8、Refer to the exhibit. An engineer is trying to block the route to 192.168.2.2 from the routing table by using the configuration that is shown. The route is still present in the routing table as an OSPF route. Which action blocks the route?
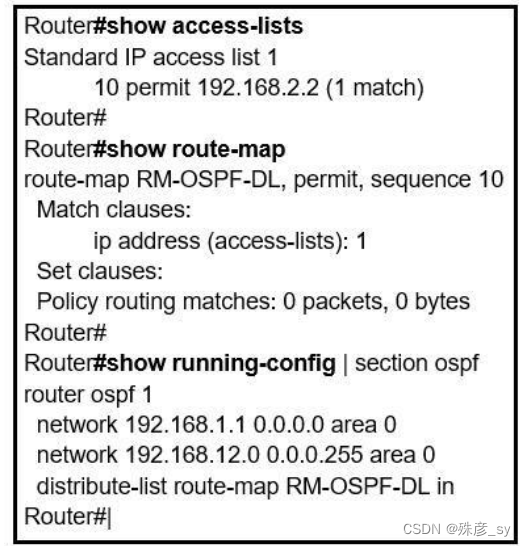
A. Use an extended access list instead of a standard access list.
B. Change sequence 10 in the route-map command from permit to deny.
C. Use a prefix list instead of an access list in the route map.
D. Add this statement to the route map: route-map RM-OSPF-DL deny 20
9、What is a prerequisite for configuring BFD?
A. Jumbo frame support must be configured on the router that is using BFD.
B. All routers in the path between two BFD endpoints must have BFD enabled.
C. Cisco Express Forwarding must be enabled on all participating BFD endpoints.
D. To use BFD with BGP, the timers 3 9 command must first be configured in the BGP routing process
10、Refer to the exhibit. R2 is a route reflector, and R1 and R3 are route reflector clients. The route reflector learns the route to 172.16.25.0/24 from R1, but it does not advertise to R3. What is the reason the route is not advertised?
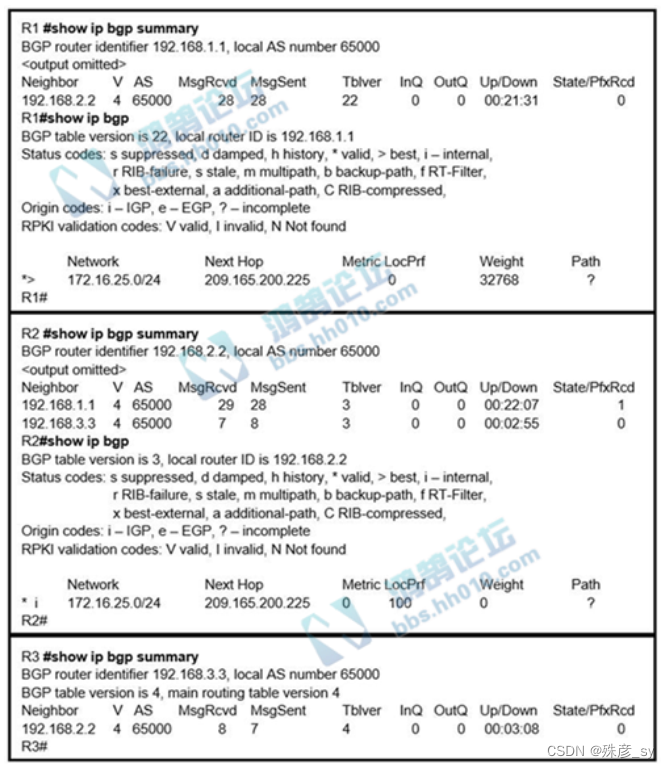
A. R2 does not have a route to the next hop, so R2 does not advertise the prefix to other clients.
B. Route reflector setup requires full IBGP mesh between the routers.
C. In route reflector setup, only classful prefixes are advertised to other clients.
D. In route reflector setups, prefixes are not advertised from one client to another
11、Refer to the exhibit. An engineer is trying to redistribute OSPF to BGP, but not all of the routes are redistributed. What is the reason for this issue?
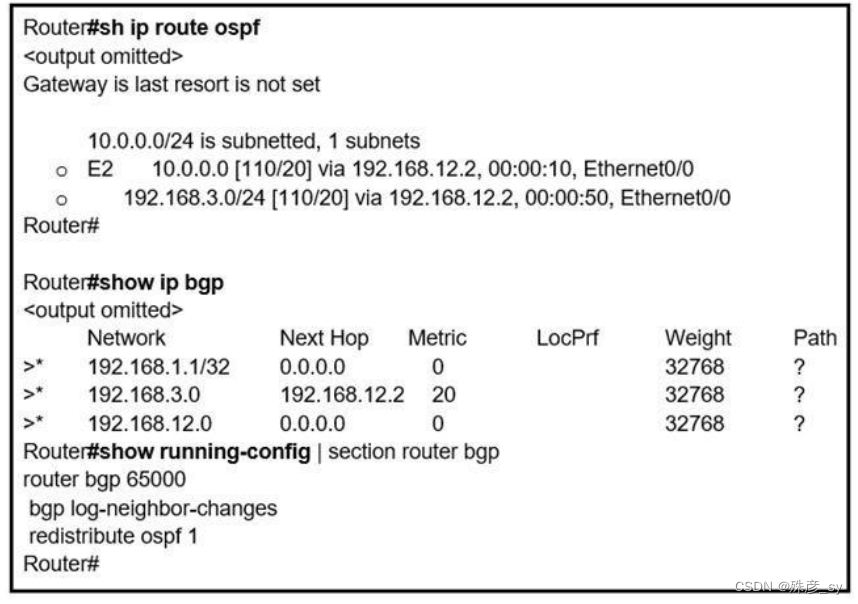
A. By default, only internal routes and external type 1 routes are redistributed into BGP
B. Only classful networks are redistributed from OSPF to BGP
C. BGP convergence is slow, so the route will eventually be present in the BGP table
D. By default, only internal OSPF routes are redistributed into BGP
12、Refer to the exhibit. In which circumstance does the BGP neighbor remain in the idle condition?
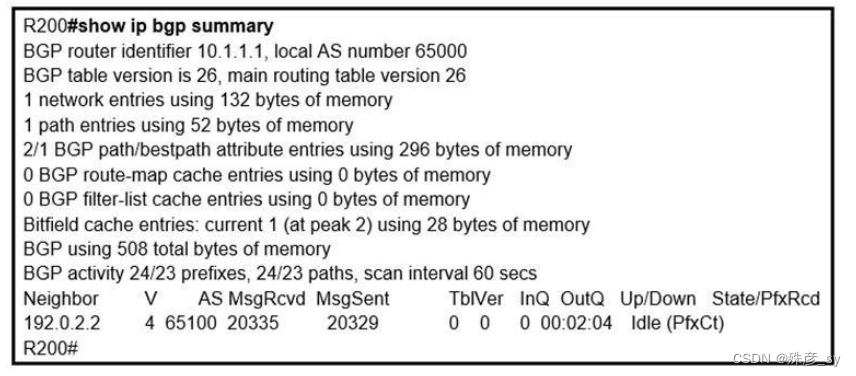
A. if prefixes are not received from the BGP peer
B. if prefixes reach the maximum limit
C. if a prefix list is applied on the inbound direction
D. if prefixes exceed the maximum limit
13、 Which attribute eliminates LFAs that belong to protected paths in situations where links in a network are connected through a common fiber?
A. shared risk link group-disjoint
B. linecard-disjoint
C. lowest-repair-path-metric
D. interface-disjoint
14、Refer to the exhibit. An engineer is troubleshooting BGP on a device but discovers that the clock on the device does not correspond to the time stamp of the log entries. Which action ensures consistency between the two times?

A. Configure the service timestamps log uptime command in global configuration mode.
B. Configure the logging clock synchronize command in global configuration mode.
C. Configure the service timestamps log datetime localtime command in global configuration mode.
D. Make sure that the clock on the device is synchronized with an NTP server.
15、Refer to the exhibit. What is the result of applying this configuration?
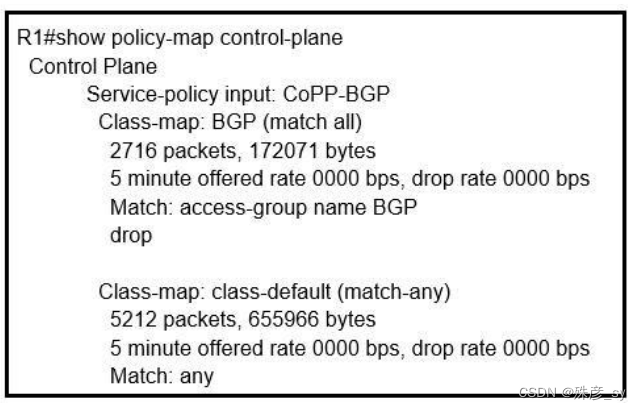
A. The router can form BGP neighborships with any other device.
B. The router cannot form BGP neighborships with any other device.
C. The router cannot form BGP neighborships with any device that is matched by the access list named “BGP”.
D. The router can form BGP neighborships with any device that is matched by the access list named “BGP”.
16、Which command displays the IP routing table information that is associated with VRF-Lite?
A. show ip vrf
B. show ip route vrf
C. show run vrf
D. show ip protocols vrf
17、Refer to the exhibit. Which subnet is redistributed from EIGRP to OSPF routing protocols?
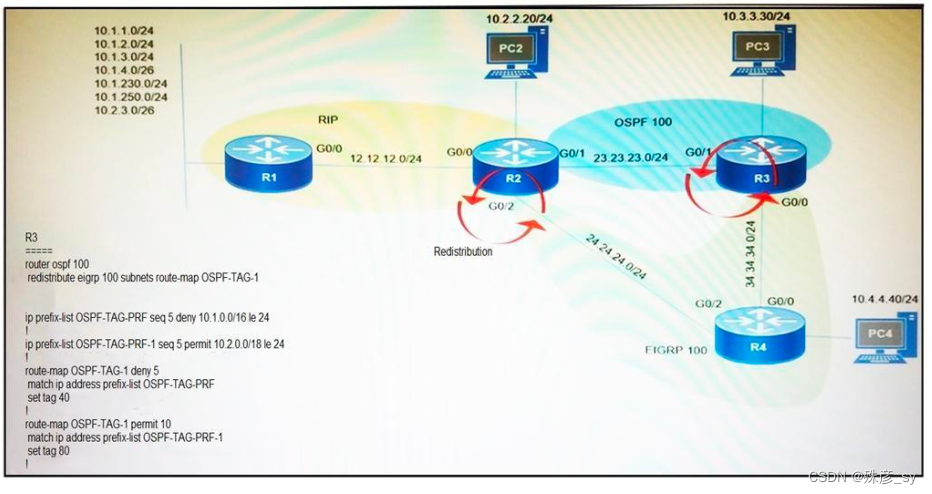
A. 10.2.2.0/24
B. 10.1.4.0/26
C. 10.1.2.0/24
D. 10.2.3.0/26
18、 Which configuration adds an IPv4 interface to an OSPFv3 process in OSPFv3 address family configuration?
A. router ospfv3 1 address-family ipv4
B. Router(config-router)#ospfv3 1 ipv4 area 0
C. Router(config-if)#ospfv3 1 ipv4 area 0
D. router ospfv3 1 address-family ipv4 unicast
19、Refer to the exhibit. Which statement about R1 is true?

A. OSPF redistributes RIP routes only if they have a tag of one.
B. RIP learned routes are distributed to OSPF with a tag value of one.
C. R1 adds one to the metric for RIP learned routes before redistributing to OSPF.
D. RIP routes are redistributed to OSPF without any changes.
20、 Refer to the exhibit. An IP SLA was configured on router R1 that allows the default route to be modified in the event that Fa0/0 loses reachability with the router R3 Fa0/0 interface. The route has changed to flow through router R2. Which debug command is used to troubleshoot this issue?
A. debug ip flow
B. debug ip sla error
C. debug ip routing
D. debug ip packet
21、 Which configuration enabled the VRF that is labeled “Inet” on FastEthernet0/0?
A. R1(config)# ip vrf Inet
R1(config-vrf)#ip vrf FastEthernet0/0
B. R1(config)#ip vrf Inet FastEthernet0/0
C. R1(config)# ip vrf Inet
R1(config-vrf)#interface FastEthernet0/0R1(config-if)#ip vrf forwarding Inet
D. R1(config)#router ospf 1 vrf Inet
R1(config-router)#ip vrf forwarding FastEthernet0/0
22、Refer to the exhibit. After redistribution is enabled between the routing protocols; PC2, PC3, and PC4 cannot reach PC1. Which action can the engineer take to solve the issue so that all the PCs are reachable?
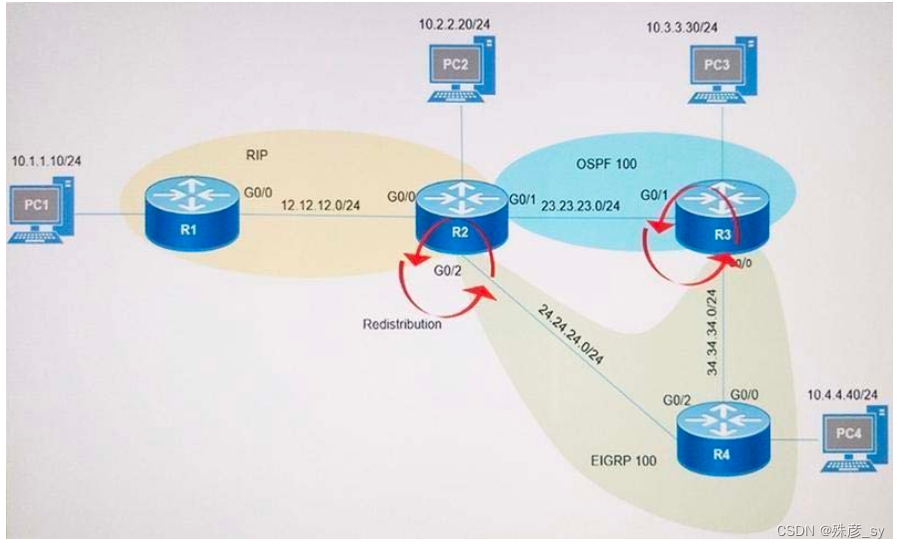
A. Set the administrative distance 100 under the RIP process on R2.
B. Filter the prefix 10.1.1.0/24 when redistributed from OSPF to EIGRP.
C. Filter the prefix 10.1.1.0/24 when redistributed from RIP to EIGRP.
D. Redistribute the directly connected interfaces on R2
23、Which command allows traffic to load-balance in an MPLS Layer 3 VPN configuration?
A. multi-paths eibgp 2
B. maximum-paths 2
C. maximum-paths ibgp 2
D. multi-paths 2
24、Refer to the exhibit. After applying IPsec, the engineer observed that the DMVPN tunnel went down, and both spoke-to-spoke and hub were not establishing.
Which two actions resolve the issue? (Choose two.)
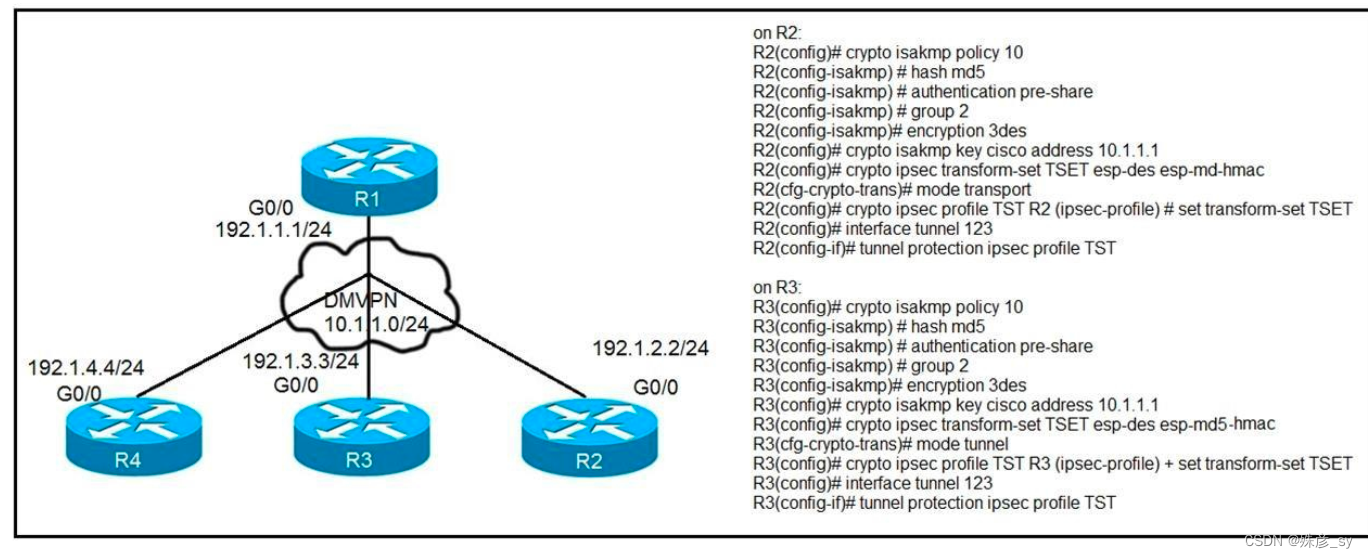
A. Change the mode from mode tunnel to mode transport on R3.
B. Remove the crypto isakmp key cisco address 10.1.1.1 on R2 and R3.
C. Configure the crypto isakmp key cisco address 192.1.1.1 on R2 and R3.
D. Configure the crypto isakmp key cisco address 0.0.0.0 on R2 and R3.
E. Change the mode from mode transport to mode tunnel on R2.
25、Which statement about route distinguishers in an MPLS network is true?
A. Route distinguishers allow multiple instances of a routing table to coexist within the edge router.
B. Route distinguishers are used for label bindings.
C. Route distinguishers make a unique VPNv4 address across the MPLS network.
D. Route distinguishers define which prefixes are imported and exported on the edge router
26、Which statement about MPLS LDP router ID is true?
A. If not configured, the operational physical interface is chosen as the router ID even if a loopback is configured.
B. The loopback with the highest IP address is selected as the router ID.
C. The MPLS LDP router ID must match the IGP router ID.
D. The force keyword changes the router ID to the specified address without causing any impact.
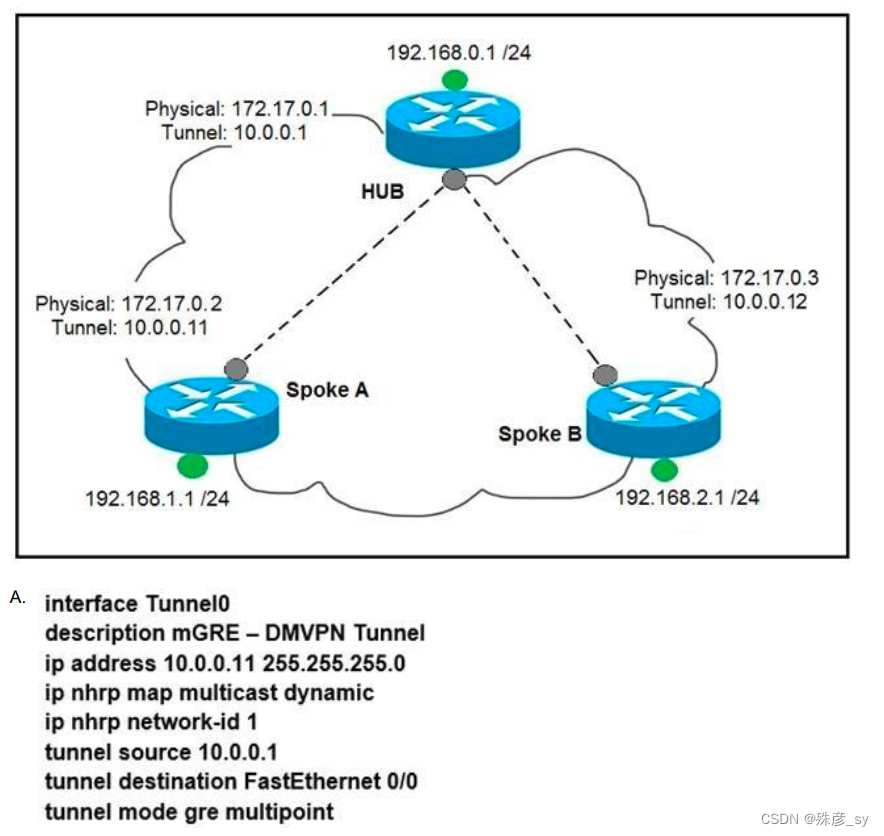
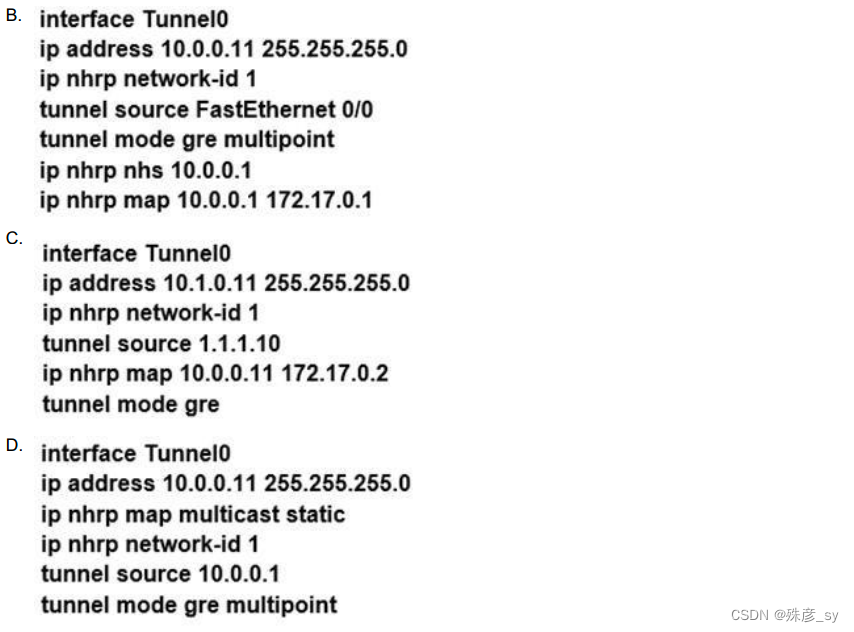
27、Refer to the exhibit. Which interface configuration must be configured on the spoke A router to enable a dynamic DMVPN tunnel with the spoke B router? B
28、Which list defines the contents of an MPLS label?
A. 20-bit label; 3-bit traffic class; 1-bit bottom stack; 8-bit TTL
B. 32-bit label; 3-bit traffic class; 1-bit bottom stack; 8-bit TTL
C. 20-bit label; 3-bit flow label; 1-bit bottom stack; 8-bit hop limit
D. 32-bit label; 3-bit flow label; 1-bit bottom stack; 8-bit hop limit
29、Refer to the exhibit. What does the imp-null tag represent in the MPLS VPN cloud?

A. Pop the label
B. Impose the label
C. Include the EXP bit
D. Exclude the EXP bit
30、 Which transport layer protocol is used to form LDP sessions?
A. UDP
B. SCTP
C. TCP
D. RDP
31、Refer to the exhibits. Phase-3 tunnels cannot be established between spoke-to-spoke in DMVPN. Which two commands are missing? (Choose two.)
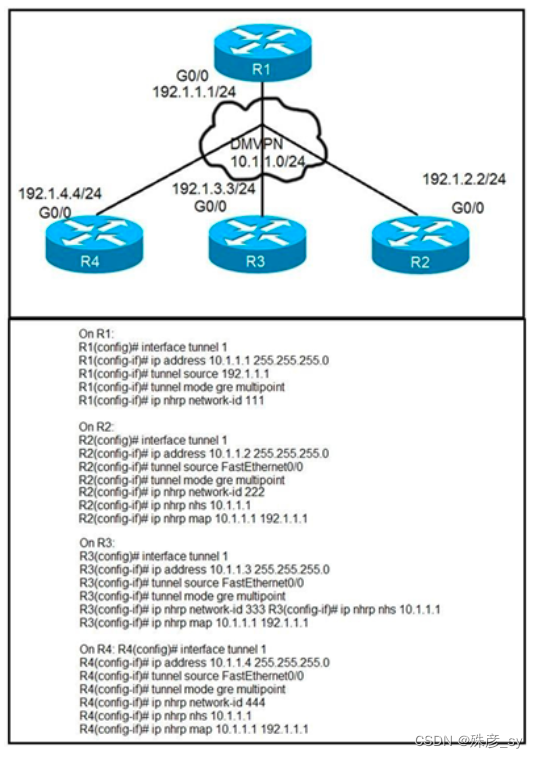
A. The ip nhrp redirect command is missing on the spoke routers.
B. The ip nhrp shortcut command is missing on the spoke routers.
C. The ip nhrp redirect command is missing on the hub router.
D. The ip nhrp shortcut command is missing on the hub router.
E. The ip nhrp map command is missing on the hub router.
32、Which protocol is used to determine the NBMA address on the other end of a tunnel when mGRE is used?
A. NHRP
B. IPsec
C. MP-BGP
D. OSPF
33、Refer to the exhibit. Which configuration denies Telnet traffic to router 2 from 198A:0:200C::1/64? A


34、Refer to the exhibit. During troubleshooting it was discovered that the device is not reachable using a secure web browser. What is needed to fix the problem?
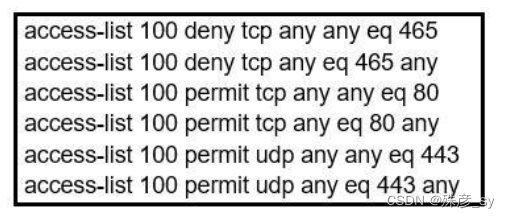
A. permit tcp port 443
B. permit udp port 465
C. permit tcp port 465
D. permit tcp port 22
35、 Refer to the exhibit. An engineer is trying to configure local authentication on the console line, but the device is trying to authenticate using TACACS+. Which action produces the desired configuration?
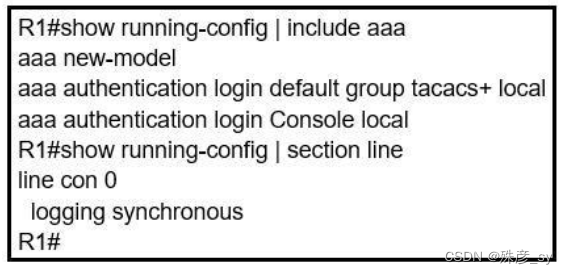
A. Add the aaa authentication login default none command to the global configuration.
B. Replace the capital “C” with a lowercase “c” in the aaa authentication login Console local command.
C. Add the aaa authentication login default group tacacs+ local-case command to the global configuration.
D. Add the login authentication Console command to the line configuration
36、Refer to the exhibit. An engineer is trying to connect to a device with SSH but cannot connect. The engineer connects by using the console and finds the displayed
output when troubleshooting. Which command must be used in configuration mode to enable SSH on the device?

A. no ip ssh disable
B. ip ssh enable
C. ip ssh version 2
D. crypto key generate rsa
37、 Which statement about IPv6 ND inspection is true?
A. It learns and secures bindings for stateless autoconfiguration addresses in Layer 3 neighbor tables.
B. It learns and secures bindings for stateless autoconfiguration addresses in Layer 2 neighbor tables.
C. It learns and secures bindings for stateful autoconfiguration addresses in Layer 3 neighbor tables.
D. It learns and secures bindings for stateful autoconfiguration addresses in Layer 2 neighbor tables.
38、While troubleshooting connectivity issues to a router, these details are noticed:
-Standard pings to all router interfaces, including loopbacks, are successful.
- Data traffic is unaffected.
- SNMP connectivity is intermittent.
- SSH is either slow or disconnects frequently.
Which command must be configured first to troubleshoot this issue?
A. show policy-map control-plane
B. show policy-map
C. show interface | inc drop
D. show ip route
39、Refer to the exhibit. Why is user authentication being rejected?

A. The TACACS+ server expects “user”, but the NT client sends “domain/user”.
B. The TACACS+ server refuses the user because the user is set up for CHAP.
C. The TACACS+ server is down, and the user is in the local database.
D. The TACACS+ server is down, and the user is not in the local database.
40、 Refer to the exhibit. Which control plane policy limits BGP traffic that is destined to the CPU to 1 Mbps and ignores BGP traffic that is sent at higher rate?
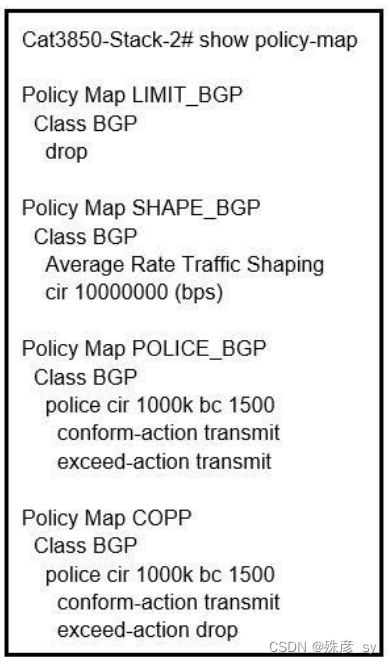
A. policy-map SHAPE_BGP
B. policy-map LIMIT_BGP
C. policy-map POLICE_BGP
D. policy-map COPP
41、Which statement about IPv6 RA Guard is true?
A. It does not offer protection in environments where IPv6 traffic is tunneled.
B. It cannot be configured on a switch port interface in the ingress direction.
C. Packets that are dropped by IPv6 RA Guard cannot be spanned.
D. It is not supported in hardware when TCAM is programmed
42、An engineer is trying to copy an IOS file from one router to another router by using TFTP. Which two actions are needed to allow the file to copy? (Choose two.)
A. Copy the file to the destination router with the copy tftp: flash: command
B. Enable the TFTP server on the source router with the tftp-server flash:
C. TFTP is not supported in recent IOS versions, so an alternative method must be used
D. Configure a user on the source router with the username tftp password tftp command
E. Configure the TFTP authentication on the source router with the tftp-server authentication local command
43、Refer to the exhibit. Users report that IP addresses cannot be acquired from the DHCP server. The DHCP server is configured as shown. About 300 total nonconcurrent users are using this DHCP server, but none of them are active for more than two hours per day. Which action fixes the issue within the current resources?

A. Modify the subnet mask to the network 192.168.1.0 255.255.254.0 command in the DHCP pool
B. Configure the DHCP lease time to a smaller value
C. Configure the DHCP lease time to a bigger value
D. Add the network 192.168.2.0 255.255.255.0 command to the DHCP pool
44、 Refer to the exhibit. ISP 1 and ISP 2 directly connect to the Internet. A customer is tracking both ISP links to achieve redundancy and cannot see the Cisco IOS IP SLA tracking output on the router console. Which command is missing from the IP SLA configuration?
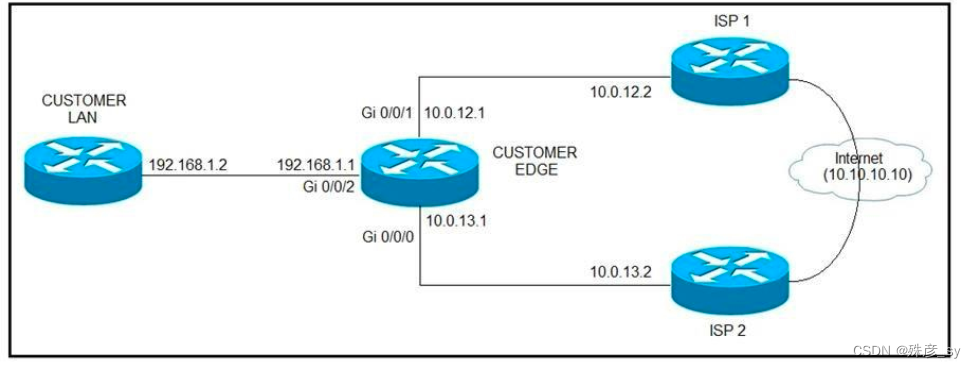
A. Start-time 00:00
B. Start-time 0
C. Start-time immediately
D. Start-time now
45、 Refer to the exhibit. An administrator noticed that after a change was made on R1, the timestamps on the system logs did not match the clock. What is the reasonfor this error?
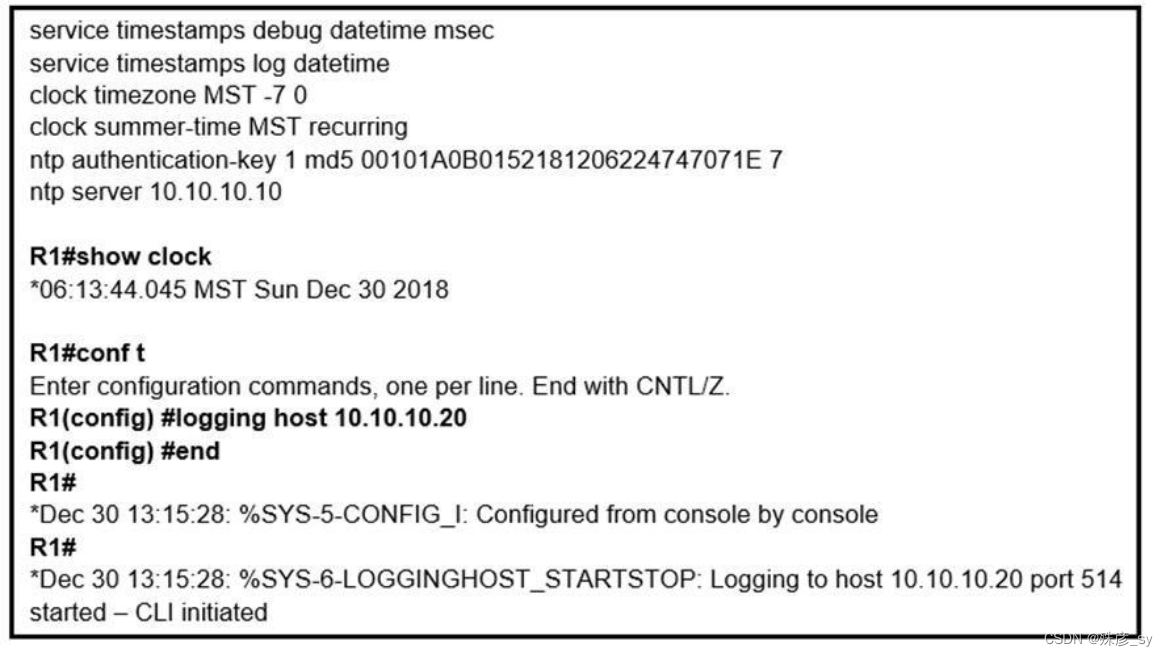
A. An authentication error with the NTP server results in an incorrect timestamp.
B. The keyword localtime is not defined on the timestamp service command.
C. The NTP server is in a different time zone.
D. The system clock is set incorrectly to summer-time hours.
46、A network engineer is investigating a flapping (up/down) interface issue on a core switch that is synchronized to an NTP server. Log output currently does not show the time of the flap. Which command allows the logging on the switch to show the time of the flap according to the clock on the device?
A. service timestamps log uptime
B. clock summer-time mst recurring 2 Sunday mar 2:00 1 Sunday nov 2:00
C. service timestamps log datetime localtime show-timezone
D. clock calendar-valid
47、When provisioning a device in Cisco DNA Center, the engineer sees the error message “Cannot select the device. Not compatible with template”. What is the
reason for the error?
A. The template has an incorrect configuration.
B. The software version of the template is different from the software version of the device.
C. The changes to the template were not committed.
D. The tag that was used to filter the templates does not match the device tag.
48、While working with software images, an engineer observes that Cisco DNA Center cannot upload its software image directly from the device. Why is the image not uploading?
A. The device must be resynced to Cisco DNA Center.
B. The software image for the device is in install mode.
C. The device has lost connectivity to Cisco DNA Center.
D. The software image for the device is in bundle mode
49、An engineer configured the wrong default gateway for the Cisco DNA Center enterprise interface during the install. Which command must the engineer run to
correct the configuration?
A. sudo maglev-config update
B. sudo maglev install config update
C. sudo maglev reinstall
D. sudo update config install
50、Refer to the exhibit. An administrator that is connected to the console does not see debug messages when remote users log in. Which action ensures that debug messages are displayed for remote logins?
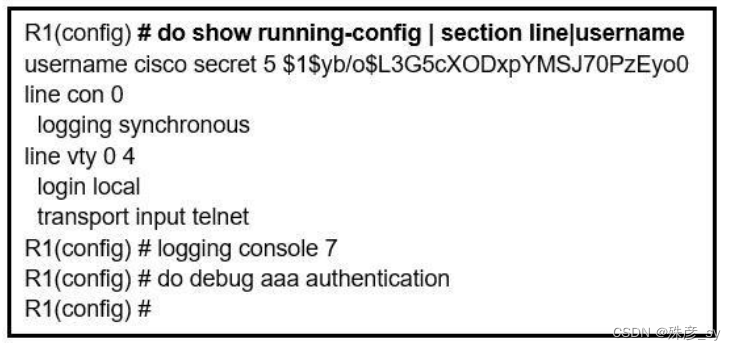
A. Enter the transport input ssh configuration command.
B. Enter the terminal monitor exec command.
C. Enter the logging console debugging configuration command.
D. Enter the aaa new-model configuration command.
